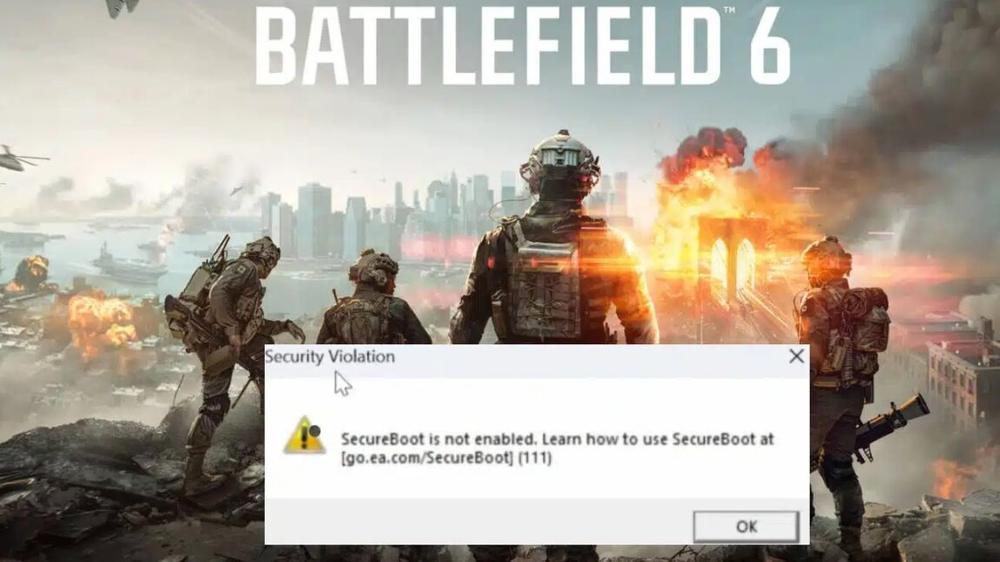
Earlier this month, EA announced that players in its Battlefield 6 open beta on PC would have to enable Secure Boot in their Windows OS and BIOS settings. That decision proved controversial among players who weren't able to get the finicky low-level security setting working on their machines and others who were unwilling to allow EA's anti-cheat tools to once again have kernel-level access to their systems.
Now, Battlefield 6 technical director Christian Buhl is defending that requirement as something of a necessary evil to combat cheaters, even as he apologizes to any potential players that it has kept away.
"The fact is I wish we didn't have to do things like Secure Boot," Buhl said in an interview with Eurogamer. "It does prevent some players from playing the game. Some people's PCs can't handle it and they can't play: that really sucks. I wish everyone could play the game with low friction and not have to do these sorts of things."
Throughout the interview, Buhl admits that even requiring Secure Boot won't completely eradicate cheating in Battlefield 6 long term. Even so, he offered that the Javelin anti-cheat tools enabled by Secure Boot's low-level system access were "some of the strongest tools in our toolbox to stop cheating. Again, nothing makes cheating impossible, but enabling Secure Boot and having kernel-level access makes it so much harder to cheat and so much easier for us to find and stop cheating."
Too much security, or not enough?
When announcing the Secure Boot requirement in a Steam forum post prior to the open beta, EA explained that having Secure Boot enabled "provides us with features that we can leverage against cheats that attempt to infiltrate during the Windows boot process." Having access to the Trusted Platform Module on the motherboard via Secure Boot provides the anti-cheat team with visibility into things like kernel-level cheats and rootkits, memory manipulation, injection spoofing, hardware ID manipulation, the use of virtual machines, and attempts to tamper with anti-cheat systems, the company wrote.
After the Battlefield 6 open beta launched, EA reported that its Javelin anti-cheat system had already "prevented 330,000 attempts to cheat or tamper with anti-cheat controls" in less than two days of play. At the same time, EA said players had reported 104,000 instances of "potential cheaters" using in-game tools, providing evidence the company says "can lead to new detection techniques and help us keep [cheaters] from impacting your experience."
"There are certain signals that we can only trust when Secure Boot is enabled," EA wrote in its report. "Secure Boot is not, and was not intended to be a silver bullet... It’s another barrier that helps us make it harder for cheat developers to create cheat programs, and makes it easier for us to detect it when they do."
Despite all these justifications for the Secure Boot requirement on EA's part, it hasn't been hard to find people complaining about what they see as an onerous barrier to playing an online shooter. A quick Reddit search turns up dozens of posts complaining about the difficulty of getting Secure Boot on certain PC configurations or expressing discomfort about installing what they consider a "malware rootkit" on their machine.
"I want to play this beta but A) I’m worried about bricking my PC. B) I’m worried about giving EA complete access to my machine," one representative Redditor wrote.
Regardless, Buhl told Eurogamer that overall the team has been "pretty happy with how the anti-cheat performed" so far, and that the anti-cheat system remains a "high priority" as the game heads toward a planned October 6 launch. "Anti-cheat never ends," Buhl said. "It's a constant cat-and-mouse game. We're never going to win. Hopefully they're never going to win. But in the end, we want to be as safe and secure as possible."
 Xiaomi lancia il suo primo robot lavapavimenti con bracci estensibili
Xiaomi lancia il suo primo robot lavapavimenti con bracci estensibili